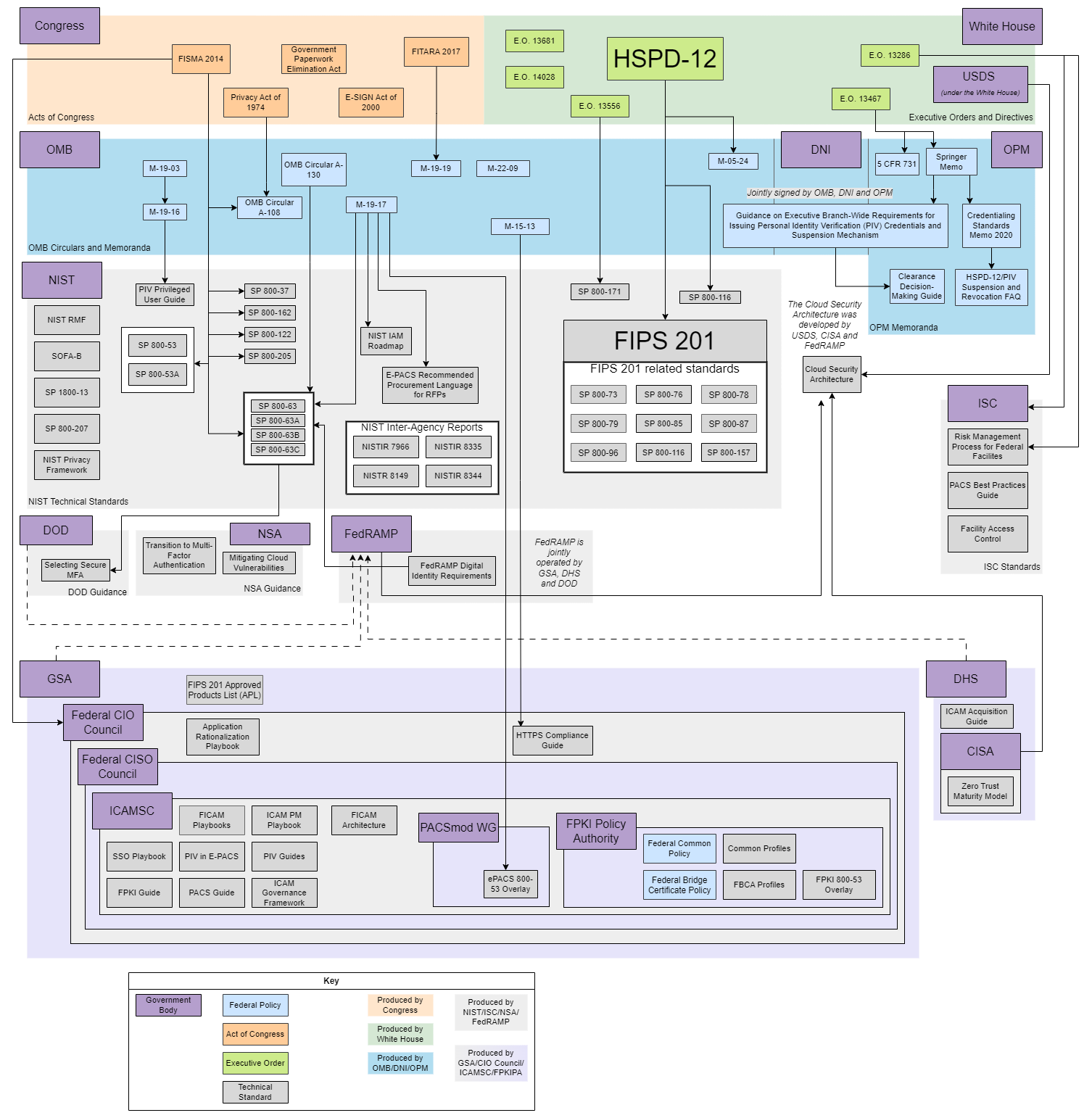
FICAM Policy Matrix
Introduction
Laws, executive policies, regulations, and government standards drive multiple federal initiatives related to Federal Identity, Credential and Access Management. IATAD maintains this policy matrix to map delegations and authorities. ICAM Partners can use this matrix to understand the origins and ultimate authority of ICAM initiatives.
Policy Overview
The policy map below presents a visual overview of the laws, policies and standards relevant to FICAM. The documents are organized according to the government body that produced it, and the relationships between the documents are illustrated by arrows connecting them.
Laws and Directives
This table lists the laws that establish or authorize the entities and activities listed in later tables.
Laws are sorted by date, from oldest to newest.
Click on the name of a law or directive to see more details about it, and for a link to the law itself.
Date: 31 Dec 1974
This Act protects certain federal government records pertaining to individuals. In particular, the Act covers systems of records that an agency maintains and retrieves by an individual's name or other personal identifier, such as a Social Security Number.
Date: 21 Oct 1998
This Act requires federal agencies to allow individuals or entities that deal with the agencies the option to submit information or transact with the agency electronically when possible and to maintain records electronically when possible. This Act specifically states that electronic records and their related electronic signatures cannot be denied legal effect, validity, or enforceability just because they are in electronic form. This Act also encourages federal government use of a range of electronic signature alternatives.
Date: 30 Jun 2000
This Act facilitates the use of electronic records and electronic signatures in interstate and foreign commerce by ensuring the validity and legal effect of electronic contracts. This act led to the creation of the Federal PKI.
Date: 03 May 2003
Amends an earlier Executive Order (E.O. 12977). Defines a central federal function to define security for physical access to federal facilities. Because physical access often involves PIV Cards, ICAMSC coordinates closely with the federal Physical Access Control System (PACS) community.
Date: 27 Aug 2004
Directive requires the development and agency implementation of a mandatory, government-wide standard for secure and reliable forms of identification for Federal employees and contractors.
Date: 30 Jun 2008
This Executive Order mandates a common background check process across the civilian, unclassified the federal government, leading to the acceptance of PIV cards across agency boundaries.
Date: 09 Nov 2010
This order establishes an open and uniform program for managing information that requires safeguarding but is not classified. The program includes standards for Identity and Access Management for Controlled Unclassified Information (CUI)
Date: 17 Oct 2014
Proposes improved security for government payments and identity theft remediation, encouraging deployment of better citizen authentication technologies for financial transactions.
Date: 18 Dec 2014
Directed NIST and OMB to provide updated guidance for the modernization of Federal IT Systems, and established the Federal CIO Council.
Date: 06 Jan 2017
Directs the head of each agency to implement a single sign-on for public websites that require user authentication as developed by the General Services Administration. Additionally, implement multi-factor authentication for remote access and accounts with elevated privileges.
Date: 21 Nov 2017
Extended the authorization for the Data Center Consolidation Act, which encourages the use of Cloud Services by Federal Agencies where appropriate. We continue to update our guidance to address the requirements of cloud implementation of federal services.
Date: 17 May 2021
Directs federal agencies to develop a plan to implement a Zero Trust Architecture, and Multi-Factor Authentication.
Federal Policies
This table lists Federal Policies and directives published by OMB. They set a strategic direction for the entire Federal Government, and are the basis for development of the standards and technical guidance documents produced to support FICAM.
Laws are sorted by date, from oldest to newest.
Click on the name of a policy to see more details about it, and for a link to the policy itself.
Date: 05 Aug 2005
This memorandum provides implementing instructions for the Directive (HSPD-12) and the Standard (FIPS-201).
Date: 14 Jan 2008
As a result of an initiative to create a more simplified system of Federal Government investigative and adjudicative procedures that applies to all persons, including contract personnel, who perform work on behalf of the government, we are providing the attached Credentialing, Suitability, and Security Clearance Decision-Making Guide. This tool is for use in adjudicative decisions for HSPD-12 credentialing [and] suitability determinations.
Date: 15 Apr 2008
Establish criteria and procedures for making determinations of suitability and for taking suitability actions during the onboarding of employees in covered positions.
Date: 31 Jul 2008
This memorandum provides final government-wide credentialing standards to be used by all Federal departments and agencies in determining whether to issue or revoke personal identity verification (PIV) cards to their employees and contractor personnel, including those who are non-United States citizens.
Date: 08 Jul 2015
This Memorandum requires that all publicly accessible Federal websites and web services only provide service through a secure connection. The strongest privacy and integrity protection currently available for public web connections is Hypertext Transfer Protocol Secure (HTTPS). Agencies must utilize PKI device certificates to protect their web servers.
Date: 02 Mar 2016
Accordingly, effective immediately, all Executive departments and agencies will apply both the basic and supplemental credentialing standards specified in the 2008 Credentialing Memo to determine initial eligibility for a PIV credential of all personnel who require a PIV, but who are not otherwise subject to a suitability determination or a determination of eligibility for access to classified information or assignment to a sensitive national security position.
Date: 28 Jul 2016
This Circular is designed to help drive the transformation of the Federal Government and the way it builds, buys, and delivers technology by institutionalizing more agile approaches intended to facilitate the rapid adoption of changing technologies, in a way that enhances information security, privacy, and management of information resources across all Federal programs and services.
Date: 23 Dec 2016
This circular describes agency responsibilities for implementing the review, reporting, and publication requirements of the Privacy Act of 1974 and related OMB policies.
Date: 10 Dec 2018
Federal law and policy establish requirements for the proper handling of PII. To both ensure compliance with those requirements and to manage privacy risks, SAOPs are required to review agency [High Value Assets] and identify those that create, collect, use, process, store, maintain, disseminate, disclose, or dispose of PII.
Date: 26 Apr 2019
This memorandum describes the process and desired outcomes for shared services such as PKI Shared Service Providers (SSPs).
Date: 21 May 2019
This memorandum sets forth the Federal Government's1 Identity, Credential, and Access Management (ICAM) policy
Date: 25 Jun 2019
This Memorandum contains requirements for the consolidation and optimization of Federal data centers in accordance with FITARA. It establishes consolidation and optimization targets and metrics for Federal agencies, as well as requirements for reporting on their progress. For FICAM, this suggests use of Identity as a Service Providers and Shared Service Providers for PKI, as discussed in the Cloud Identity Playbook.
Date: 15 Dec 2020
[T]he following credentialing standards procedures [...] promote defined goals in agency eligibility determinations to issue HSPD-12 personal identity verification (PIV) credentials for access to federally controlled facilities and information systems: the protection of the life, safety, property, or health of employees, contractors, vendors or visitors to Federal facilities; the protection of the Government's physical assets, information systems, records, including privileged, proprietary, financial or medical records; and the privacy of the individuals whose data the Government holds in its systems.
Date: 26 Jan 2022
This strategy places significant emphasis on stronger enterprise identity and access controls, including multi-factor authentication (MFA).
Date: 17 Apr 2023
The FBCA exists to facilitate trusted electronic business transactions for Federal organizations. To facilitate the missions of the organizations, interoperability is offered to non-Federal entities.
Date: 17 Apr 2023
The scope of this U.S. Federal PKI Common Policy Framework CP includes the Certification Authorities used for issuing and managing certificates that are valid to the Federal Common Policy CA on behalf of federal executive branch agencies. This CP applies to certificates issued to CAs, devices, and federal employees, contractors and other affiliated personnel.
This Memorandum provides guidance for Federal agencies to modernize the processes by which individuals may request access to, and consent to the disclosure of, records protected under the Privacy Act of 1974. As required by the Creating Advanced Streamlined Electronic Services for Constituents Act of 2019 ('CASES Act'), this guidance outlines the responsibilities of agencies for accepting access and consent forms provided in a digital format from individuals who are properly identity-proofed and authenticated.
Federal Technical Guidance
This table lists Technical Guidance published under ICAM. They provide technical details to support consistent, secure and effective implementation of the policies.
Click on the name of a guidance document to see more details about it, and for a link to the document itself.
Date: 31 Jul 2006
In order to build the necessary PIV infrastructure to support common unified processes and government-wide use of identity credentials, NIST developed this test guidance document that ensures interoperability of PIV data.
Date: 29 Dec 2006
The purpose of this document is to present recommendations for Personal Identity Verification (PIV) card readers in the area of performance and communications characteristics to foster interoperability.
Date: 06 Apr 2010
This guideline assists federal agencies in protecting the confidentiality of a specific category of data commonly known as PII. This document provides practical, context-based guidance for identifying PII and determining what level of protection is appropriate for each instance of PII. The document also suggests safeguards that may offer appropriate levels of protection for PII and provides recommendations for developing response plans for breaches involving PII.
Date: 11 Jul 2013
This document [...] describes technical acquisition and formatting specifications for the PIV system, including the PIV Card itself. It also establishes minimum accuracy specifications for deployed biometric authentication processes.
Date: 26 Mar 2014
The sole purpose of this document is to provide detailed technical and security guidance for leveraging PIV and PIV-I authentication mechanisms in a federal agency PACS to comply with directives such as [OMB M-11-11] and to provide interoperability across the federal enterprise, respectively.
Date: 19 Dec 2014
This recommendation provides technical guidelines for the implementation of standards-based, secure, reliable, interoperable public key infrastructure (PKI) based identity credentials that are issued by Federal departments and agencies to individuals who possess and prove control over a valid PIV Card.
Date: 24 Feb 2015
This document provides language for E-PACS related procurements to ensure compliance with applicable policies
Date: 29 May 2015
This document contains the technical specifications needed for the mandatory and optional cryptographic keys specified in FIPS 201-2 as well as the supporting infrastructure specified in FIPS 201-2 and the related NIST Special Publication 800-73-4, Interfaces for Personal Identity Verification [SP800-73], and NIST SP 800-76-2, Biometric Specifications for Personal Identity Verification [SP800-76], that rely on cryptographic functions.
Date: 15 Oct 2015
The purpose of this document is to assist organizations in understanding the basics of Secure Shell (SSH) and SSH access management in an enterprise, focusing on the management of SSH user keys.
Date: 01 Dec 2015
The Best Practices for Planning and Managing Physical Security Resources is a guide intended to provide an introduction and understanding of the most efficient processes and procedures to effectively allocate resources to implement physical security programs within Federal departments and agencies.
Date: 12 Feb 2016
This document, SP 800-73, contains the technical specifications to interface with the smart card to retrieve and use the PIV identity credentials.
Date: 12 Feb 2016
The purpose of this SP is to provide appropriate and useful guidelines for assessing the reliability of issuers of PIV Cards and Derived PIV Credentials.
Date: 21 Apr 2016
This white paper further explains the need for multi-factor PIV-based user authentication to take the place of password-based single-factor authentication for privileged users. It also provides best practices for agencies implementing PIV authentication for privileged users
Date: 11 Aug 2016
This paper [...] outlines a process intended to support the evaluation of biometric authenticators and—ultimately—multiple authentication mechanisms.
Date: 01 Nov 2016
The Risk Management Process for Federal Facilities: An Interagency Security Committee Standard (Standard), 2nd Edition defines the criteria and processes that those responsible for the security of a facility should use to determine its facility security level (FSL) and provides an integrated, single source of physical security countermeasures for all Federal facilities.
Date: 12 Jan 2018
Describes trust frameworks for identity federations, which provide a secure method for leveraging shared identity credentials across communities of similarly-focused online service providers.
Date: 31 Jan 2018
This document provides revised guidance and requirements on digital identity capabilities in support of achieving and maintaining a Federal Risk and Authorization Management Program (FedRAMP) security authorization.
Date: 19 Apr 2018
This document provides the organizational codes for federal agencies to establish the Federal Agency Smart Credential Number (FASC-N) that is required to be included in the FIPS 201 Card Holder Unique Identifier. SP 800-87 is a companion document to FIPS 201.
Date: 29 Jul 2018
This recommendation provides a technical guideline to use Personal Identity Verification (PIV) Cards in facility access; enabling federal agencies to operate as government-wide interoperable enterprises.
Date: 20 Dec 2018
This publication describes the Risk Management Framework (RMF) and provides guidelines for applying the RMF to information systems and organizations. The RMF provides a disciplined, structured, and flexible process for managing security and privacy risk that includes information security categorization; control selection, implementation, and assessment; system and common control authorizations; and continuous monitoring. The RMF includes activities to prepare organizations to execute the framework at appropriate risk management levels. The RMF also promotes near real-time risk management and ongoing information system and common control authorization through the implementation of continuous monitoring processes; provides senior leaders and executives with the necessary information to make efficient, cost-effective, risk management decisions about the systems supporting their missions and business functions; and incorporates security and privacy into the system development life cycle. Executing the RMF tasks links essential risk management processes at the system level to risk management processes at the organization level. In addition, it establishes responsibility and accountability for the controls implemented within an organization's information systems and inherited by those systems.
Date: 01 Feb 2019
This sixth edition of the Common Sense Guide to Mitigating Insider Threats provides the current recommendations of the CERT Division (part of Carnegie Mellon University's Software Engineering Institute), based on an expanded corpus of more than 1,500 insider threat cases and continued research and analysis. It introduces the topic of insider threats, describes its intended audience, outlines changes for this edition, defines insider threats, and outlines current trends. The guide then describes 21 practices that organizations should implement to prevent and detect insider threats, as well as case studies of organizations that failed to do so.
Date: 01 Feb 2019
The goal of this document is to enable any organization, including the SLTT Community, to spend its resources wisely on thoughtful and well-specified ICAM procurement activities that result in an ICAM enabled system that includes multifactor authentication.
Date: 01 Jun 2019
This playbook is a practical guide for application rationalization and IT portfolio management under the federal government's Cloud Smart initiatives. Application rationalization will help federal agencies mature IT portfolio management capabilities, empower leaders to make informed decisions, and improve the delivery of key mission and business services. It requires buy-in from stakeholders across the enterprise, including senior leaders, technology staff members, cybersecurity experts, business leads, financial practitioners, acquisition and procurement experts, and end user communities. Rationalization efforts rely on leadership support and continual engagement with stakeholders to deliver sustainable change.
Date: 18 Jun 2019
This document aims to provide federal agencies with a guide to attribute considerations with Attribute Evaluation Scheme examples for access control.
Date: 02 Aug 2019
This guideline provides federal agencies with a definition of ABAC. ABAC is a logical access control methodology in which authorization to perform a set of operations is determined by evaluating attributes associated with the subject, object, requested operations, and, in some cases, environment conditions against policy, rules, or relationships that describe the allowable operations for a given set of attributes.
Date: 30 Aug 2019
These guidelines provide technical requirements for federal agencies implementing digital identity services and are not intended to constrain the development or use of standards outside of this purpose. The guidelines cover identity proofing and authentication of users (such as employees, contractors, or private individuals) interacting with government IT systems over open networks. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols, federation, and related assertions.
Date: 08 Jan 2020
The Privacy Framework is a voluntary tool intended to help organizations identify and manage privacy risk to build innovative products and services while protecting individuals' privacy. The Privacy Framework approach to privacy risk is to consider privacy events as potential problems individuals could experience arising from system, product, or service operations with data, whether in digital or non-digital form, through a complete lifecycle from data collection through disposal.
Date: 22 Jan 2020
This document contains specific recommendations for improving ICAM practices to reduce cloud vulnerabilities.
Date: 11 Aug 2020
This document is intended to describe zero trust for enterprise security architects. Zero trust architecture depends on well strong authentication of all entities within the the environment, and well defined authorization rules.
Date: 01 Oct 2020
U.S. Government Agencies and their partners who want to integrate secure alternatives to PIV-based authentication need to support authorized users who will be employing personally owned or partner-owned devices, such as smart phones and home or non-government office computers, to access government or partner information systems containing sensitive information. By using the objective criteria in this guidance, government organizations can make better informed decisions about which multi-factor solutions meet their particular needs. And by following the practical guidelines, users can reduce their risk exposure and become harder targets for malicious threat actors.
Date: 10 Dec 2020
This guideline provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations, assets, individuals, other organizations, and the Nation from a diverse set of threats.
Date: 17 Dec 2020
This document provides guidance for federal Executive Branch departments and agencies regarding access control requirements and options for individuals entering federally occupied space
Date: 24 Dec 2020
[T]he purpose of this document is to assist those entities responsible for physical and cyber security: 1. Provide minimum applicable IT security controls and related supplemental guidance to appropriately secure and administer ePACS 2. Establish a relationship between IT system security controls and ePACS operational configurations using a standardized risk-based approach 3. Develop an initial foundation for an ePACS operational assessment by providing supplemental guidance for the implementation of authentication mechanisms in ePACS as defined in NIST [SP 800-116] 4. Define initial responsibilities for implementation and use of this overlay
Date: 01 Jan 2021
Attached are answers to some anticipated Frequently Asked Questions to assist you in successfully implementing the Credentialing Procedures guidance. In particular, we call your attention FAQ No. 13, which reminds agencies of their obligation to report HSPD-12 fields into CVS.
Date: 06 Jan 2021
This version of the FICAM Architecture encompasses the enterprise ICAM policies, technologies, and system approaches for government employees, contractors, and authorized partners.
Date: 28 Jan 2021
This publication provides guidance for operators of non-federal (e.g. commercial) systems hosting Controlled Unclassified Information (CUI). It includes several FICAM relevant requirements.
Date: 08 Feb 2021
This document includes a survey of authentication mechanisms, establishing the need and basis for authentication metrology (quantification), as well as key factors in determining strength and management requirements when assessing an authentication system in a given environment.
Date: 12 Feb 2021
The Enterprise Single Sign-On (SSO) Playbook is a practical guide to help federal agencies implement or modernize an SSO service for federal employee access to government applications.
Date: 26 Feb 2021
While many NIST [SP 800-53] controls apply to FPKI service operators as written, some controls require specific interpretation or augmentation. This overlay leverages [COMMON] to tailor appropriate [SP 800- 53] controls to facilitate implementation.
Date: 16 Jun 2021
This report informs [Public Safety Organizations] about [Identity as a Service] and how they can benefit from it.
Date: 25 Aug 2021
This NIST Cybersecurity Practice Guide describes how organizations can implement Mobile SSO technologies to enhance public safety mission capabilities by using standards-based commercially available or open-source products.
Date: 01 Sep 2021
The ICAM Governance Framework Working Group, composed of ICAM practitioners from several federal agencies, developed this ICAM Governance Framework as a tool to help agencies build and improve ICAM governance structures, processes, and policies.
Date: 01 Jan 2022
This document establishes a standard for a Personal Identity Verification (PIV) system that meets the control and security objectives of Homeland Security Presidential Directive-12.
Date: 25 Jan 2022
This guideline provides a set of procedures for conducting assessments of security controls and privacy controls employed within federal information systems and organizations. The assessment procedures, executed at various phases of the system development life cycle, are consistent with the security and privacy controls in NIST Special Publication 800-53, Revision 5.
Date: 01 Jun 2022
[The] Cloud Security Technical Reference Architecture [illustrates] recommended approaches to cloud migration and data protection for agency data collection and reporting that leverages Cloud Security Posture Management (CSPM). Provides specific guidance on implementation of ICAM controls for policy enforcement.
Date: 10 Jun 2022
The ICAM Program Management 101 explains how to plan and implement an Identity, Credential, and Access Management (ICAM) Program, as outlined in the Federal Identity, Credential, and Access Management (FICAM) Architecture.
Date: 30 Sep 2022
This document specifies the profiles for certificates and CRLs issued under the X.509 Certificate Policy for the U.S. Federal PKI Common Policy Framework [COMMON] and that have a trust path to the Federal Common Policy CA operated by the Federal PKI Management Authority.
Date: 18 Oct 2022
This document specifies the profiles for X.509 certificates and certificate revocation lists (CRLs) associated with CAs cross-certified with the Federal Bridge Certification Authority (FBCA).
Date: 16 Dec 2022
These guidelines provide technical requirements for federal agencies implementing digital identity services and are not intended to constrain the development or use of standards outside of this purpose. The guidelines cover identity proofing and authentication of users (such as employees, contractors, or private individuals) interacting with government IT systems over open networks. They define technical requirements in each of the areas of identity proofing, registration, authenticators, management processes, authentication protocols, federation, and related assertions.
Date: 16 Dec 2022
This guideline focuses on the enrollment and verification of an identity for use in digital services. Central to this is a process known as identity proofing in which an applicant provides evidence to a credential service provider (CSP) reliably identifying themselves, thereby allowing the CSP to assert that identification at an Identity Assurance Level (IAL). This document defines technical requirements for each of the three IALs.
Date: 16 Dec 2022
These guidelines focus on the authentication of subjects interacting with government systems over open networks, establishing that a given claimant is a subscriber who has been previously authenticated. The result of the authentication process may be used locally by the system performing the authentication or may be asserted elsewhere in a federated identity system. This document defines technical requirements for each of the three Authentication Assurance Levels (AALs).
Date: 16 Dec 2022
These guidelines provide technical requirements for federal agencies implementing digital identity services and are not intended to constrain the development or use of standards outside of this purpose. This guideline focuses on the use of federated identity and the use of assertions to implement identity federations. Federation allows a given CSP to provide authentication and (optionally) subscriber attributes to a number of separately-administered relying parties. Similarly, relying parties may use more than one CSP.
Date: 29 Dec 2022
This Cloud Identity Playbook is a practical guide to assist federal agencies as they start to or further expand the use of workforce Identity, Credential, and Access Management (ICAM) services in a cloud operating model.
Date: 29 Dec 2022
This Digital Identity Risk Assessment playbook helps federal agency Chief Information Officer (CIO) and Chief Information Security Officer (CISO) teams and business application owners to update and maintain consistent processes; determine whether an agency application requires a DIRA; integrate DIRA into agency Risk Management Framework (RMF) processes; and learn practices to implement DIRA processes.
Date: 23 Feb 2023
The Risk Management Framework provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. The risk-based approach to control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. Managing organizational risk is paramount to effective information security and privacy programs; the RMF approach can be applied to new and legacy systems, any type of system or technology (e.g., IoT, control systems), and within any type of organization regardless of size or sector.
Date: 11 Apr 2023
CISA's Zero Trust Maturity Model (ZTMM) provides an approach to achieve continued modernization efforts related to zero trust within a rapidly evolving environment and technology landscape. Section 5.1, Identity, presents a maturity model for Identity Management in the context of Zero Trust.
Date: 21 Apr 2023
[A] roadmap for developing new and updating existing NIST guidance related to Identity and Access Management (ICAM).
This FPKI 101 describes the structure, purpose, and current operational status of the FPKI.
The Physical Access Control System (PACS) 101 will help you understand concepts related to Federal Identity, Credential, and Access Management-compliant PACSs.
This Personal Identity Verification (PIV) 101 is intended to help you understand the purpose and uses of a PIV credential at your organization.
This site contains a web-friendly version of the White House Office of Management and Budget memorandum M-15-13, “A Policy to Require Secure Connections across Federal Websites and Web Services”, and provides technical guidance and best practices to assist in its implementation. It requires use of a publicly trusted certificate for federal web services.
The Approved Products List (APL) contains the official list of products tested for conformance to PIV Standards.