Personal Identity Verification Card 101
Introduction
This Personal Identity Verification (PIV) 101 is intended to help you understand the purpose and uses of a PIV credential at your organization. This PIV 101 focuses on using PIV credentials for logical access such as authenticating to networks or applications or digitally signing and encrypting. Using PIV for physical access is available in the PACS 101.
If you cannot find a particular topic, it may still be in development. Review the Issues for questions and lessons that are in progress. Create a new Issue to ask a question or share information with others.
Read on to learn more about PIV credentials.
What Is a PIV Credential?
A PIV credential is a U.S. federal government-wide credential used to access federally controlled facilities and information systems at the appropriate security level.
PIV credentials have certificates and key pairs, pin numbers, biometrics like fingerprints and pictures, and other unique identifiers. When these items are put together in a PIV credential, the credential provides the capability to implement multifactor authentication for networks, applications, and buildings.
What Information Is In This PIV 101?
This 101 covers PIV credential basics, including:
- What PIV is, contains, and looks like.
- The basics of getting started with PIV credentials.
Implementation practices for using PIV for network authentication (smart card logon) are found under implementations.
Who is eligible for a PIV credential?
The OPM credentialing standards outline procedures departments and agencies must use to determine PIV eligibility which at its most basic level is those needing physical or logical access to Federally controlled facilities and/or Federal IT systems for six months or more. The following communities of users are required to go through a PIV eligibility personnel risk assessment:
- Federal employees and employees of government contractors who are performing work for or on behalf of a Federal department or agency;
- Members of the armed forces;
- Non-appropriated fund employees and specific categories of individuals unique to a particular agency, such as guest researchers, volunteers, or employees on temporary appointments likely to continue for at least six months;
- Intermittent or seasonal workers whose affiliation or seasonal schedule is expected to extend beyond six months on a non-continuous basis.
Short-term workers requiring physical or logical access to federally controlled facilities or Federal IT systems for less than six months are not currently subject to this criteria. Departments and agencies should document short-term worker credential eligibility requirements in a local policy. An agency’s local policy may be to submit the individual to the PIV eligibility process to manage risk better, but it is not required. After a favorable determination of a short-term worker, departments and agencies may issue an alternative authenticator, such as a PIV Interoperable credential or an alternative authenticator.
This is a plain-language description of the PIV eligibility process and not an official standard. Please refer to the OPM credentialing standards for in-depth information on PIV applicability and eligibility, such as the adjudicative criteria, reciprocal acceptance of eligibility, and standards and procedures for suspending PIV eligibility.
Why Is PIV Usage Important?
Agency security is enhanced when PIV credentials are used for authentication to agency systems and facilities. PIV credentials allow for a high level of assurance in the individuals who that access your resources, because the credentials are only issued by trusted providers to individuals who that have been verified in person. PIV credentials are highly resistant to identity fraud, tampering, counterfeiting, and exploitation.
PIV credentials are standardized as well. PIV credentials might be issued by different organizations using different commercial or open source products, on different form factors (cards, mobile devices, etc.). However, PIV credentials are standardized—every PIV credential is required to have specific information, using technology that is interoperable.
Your PIV credential from one agency will have the same basic required format, information, and technology as a PIV credential from your partner agencies. This allows us to trust each other, share applications, and architect and implement systems using common patterns for authentication.
What Systems Should Use PIV?
Any system at your organization that requires heightened security for determining who should gain access can and should use PIV for authentication. While PIV credentials can be used for authentication on almost any system, they are especially useful for systems that protect sensitive information.
PIV should be used for:
- Privileged users access to servers, networks, and applications;
- Network authentication;
- Application authentication for all users of an application that protects or contains sensitive information; and
- Access to facilities and buildings.
Where Can I Find the Standards?
Review the information on this site if you are interested in PIV credentials or work on using PIV credentials.
If you are interested in the bits and bytes of PIV credentials, you can review the standards (see below), particularly if you develop products such as hardware or software that are specific to PIV credentials for the U.S. federal government. (For most users and engineers, the standards may be too detailed for your needs.)
To review the standards, there is a National Institute of Standards and Technology (NIST) website with all PIV-related standards. Here are links to some of the most common standards:
- FIPS 201 specifies the issuance and management of PIV credentials.
- NIST Special Publication 800-73, “Interfaces for Personal Identity Verification” specifies the interface and data elements of PIV credentials.
- NIST Special Publication 800-76, “Biometric Data Specification for Personal Identity Verification” specifies the technical acquisition and formatting requirements for biometric data of PIV credentials.
How Can I Test a PIV Card?
The Card Conformance Tool (CCT) can remotely test PIV and Personal Identity Verification–Interoperable (PIV-I) on several common operating systems. The purpose of the CCT is to validate that commercially available PIV and PIV-I comply with relevant standards.
PIV Overview
There are two main categories for the features of a PIV credential:
Physical Features
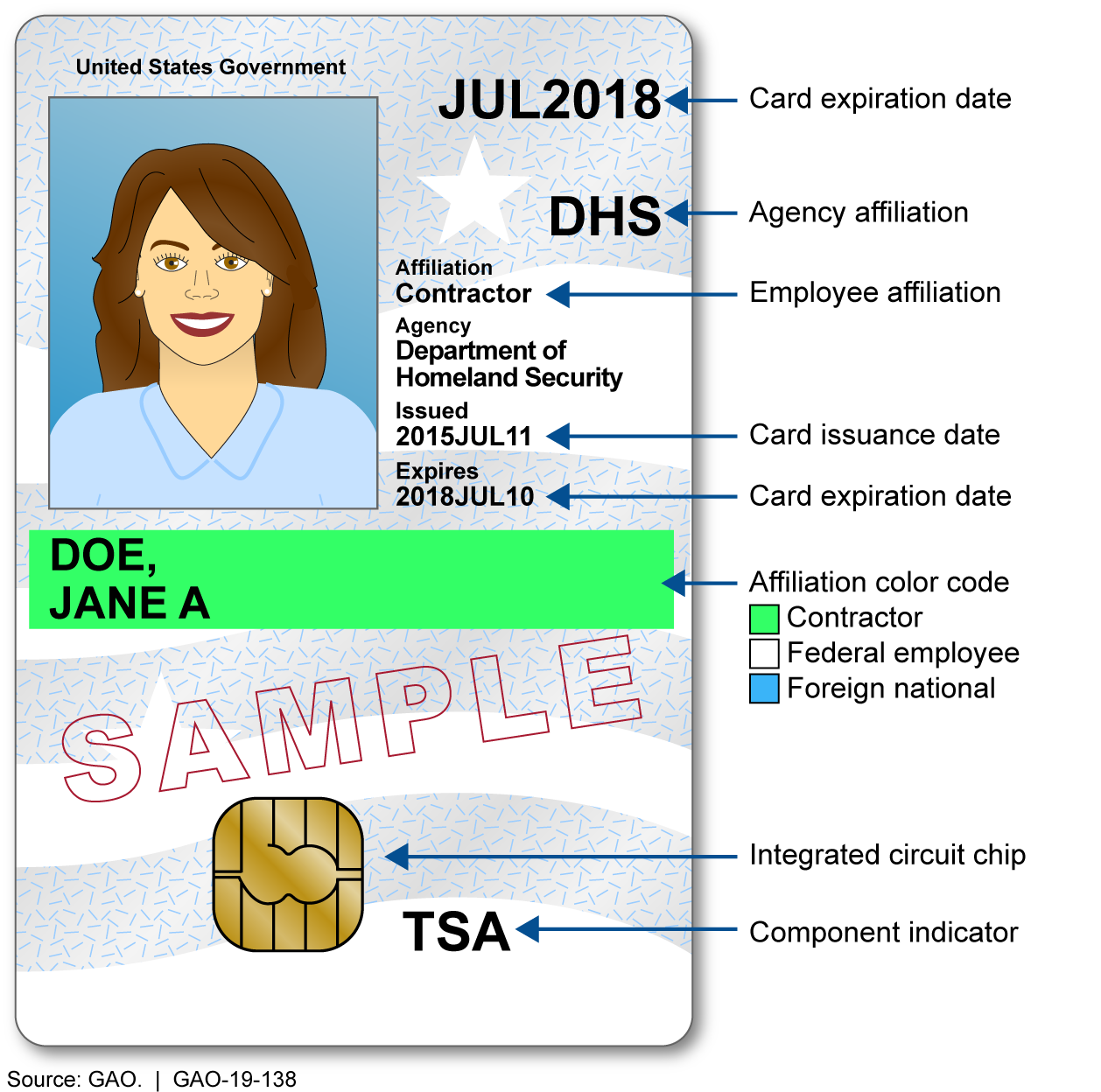
An example of a PIV credential can be seen above.
The image shows the standard placement for information such as photograph, name, affiliation, expiration date, organization, and the chip.
PIV credentials also contain at least one security feature that aids in reducing counterfeiting, is resistant to tampering, and provides visual evidence of tampering attempts such as optical varying structures or inks, laser etching, holographic images, and watermarks.
Electronic Features
What is the chip on your PIV credential? In the easiest terms, it’s a computer. It holds information very securely and can process data. The chip is also called a secure element.
Do you have a debit card with a chip or a smartphone with a SIM card?
These are both examples of similar technology that we use every day in our lives and help us secure information. You can’t use your PIV credential to withdraw money, nor do you use your debit card to log in to your computer or federal applications—but you can see how similar technology is used every day.
Most applications that use PIV credentials leverage information stored on the chip and we call this information the logical elements. These elements are defined in the NIST Special Publication 800-73 series document.
The following electronic elements authenticate the PIV credential as a device:
- Cardholder Unique Identifier (CHUID), which is a digitally signed Federal Agency Smart Card Number (FASC-N) plus other data that can be used.
- Card Authentication, which is a certificate and key pair that can be used to verify that the PIV credential was issued by an authorized entity, has not expired, and has not been revoked.
The following electronic elements authenticate YOU as the user:
- Photograph, which is stored on the chip, signed digitally, and allows a person to confirm that the printed photo on the card has not been altered.
- Biometric Identity Information such as fingerprints or iris/eye templates, which can be used to verify you.
- PIV Authentication, which is a certificate and key pair that can be used to verify that the PIV credential was issued by an authorized entity, has not expired, has not been revoked, and the holder of the credential (YOU) is the same individual it was issued to.
The following electronic elements are for usage by YOU:
- Digital Signature, which is a certificate and key pair that allows YOU to digitally sign a document or email, providing both integrity and non-repudiation.
- Encryption, which is a certificate and key pair that allows YOU to digitally encrypt documents or email with your colleagues in the federal government or with government partners, providing confidentiality through ensuring that only authorized parties can read the document or email.
The Card Authentication, PIV Authentication, Digital Signature, and Encryption all leverage four separate certificates and key pairs issued from certificate authorities that are audited and certified by the Federal Public Key Infrastructure (FPKI).
Example Forms
Provided below are links to example forms you can use as templates to create or update your own PIV acceptance and agreement forms.
- Digital Certificate user agreement
- USAccess acknowledgment
- DoD PKI Certificate Acceptance DD From 2842
PIV Readers and Middleware
You need two items to begin using your PIV credential:
- A card reader (hardware)
- Middleware (software) that works with your computer
With just their PIV credential, a card reader, and middleware, your users can log in to websites that are PIV enabled, digitally sign email and documents and files, and encrypt!
Card Readers
A card reader is exactly what the name suggests: a piece of hardware that helps read the card.
A card reader is the hardware that supplies power to the chip and allows the computer operating system to talk to the PIV credential chip operating system.
Card readers are available in many shapes and sizes to fit both the PIV credential and to plug into your computer. There is a card reader that will work for any shape and size computer you use, including card readers for USB and microUSB ports. Examples of readers include fold-up readers, desk readers, keyboard readers, tablet readers, and laptop readers.
ISO 7816
If you need to buy a card reader for computers, you will need one that specifies support for ISO 7816.
You can buy a card reader for personal use from a number of commercial online retailers. When buying card readers for your agency, you can use GSA Advantage to directly purchase the card readers.
Before you buy a card reader, look around and ensure that you don’t already have one. A large portion of government laptops already have card readers, and desktop computers may have keyboards with built-in readers.
Mac OSX or Linux-based computers often don’t have card readers built in. If this is the case, find a card reader option that works for you. Let’s move on to middleware.
Middleware
For PIV credentials, middleware refers to the computer software or drivers that allow the computer to interact with the PIV credentials to support authentication, digital signatures, encryption, and integrations with your software tools.
For common PIV credential usage scenarios, the table below outlines the general smartcard middleware available as open or government source or included in operating systems for use scenarios. Commercial options for PIV middleware are available and the list of NIST-certified PIV middleware can be viewed here on the NIST website.
Consider how to support your email client software and virtual private network software, and think about which browsers are used if you’re choosing middleware for all your agency enterprise users.
| Name | Operating System and Versions | Support | Considerations |
|---|---|---|---|
| Windows mini-driver | Windows 7, Windows 8, Windows 10, Windows 2008, Windows 2012 | Yes | Included in Windows operating systems and requires no installation. Does not include the functionality to perform full lifecycle management of a PIV credential. Does not support using your PIV credential with non-Microsoft cryptographic service providers such as those used by Mozilla Firefox browser. |
| OpenSC | Mac OSX 10.5, Mac OSX 10.6, Mac OSX 10.7, Mac OSX 10.9, Mac OSX 10.10, Windows (32-bit and 64-bit), Linux, *nix versions vary | Open Source | Open source software. Limited commercial support for maintenance and patching. Supports PKCS#11; for example, as used by Mozilla Firefox browser. Use OpenSC versions greater than 0.20.0 to reduce authentication errors to servers using TLS 1.3. |
| Smart Card Services | Mac OSX 10.6, Mac OSX 10.7, Mac OSX 10.9, Mac OSX 10.10 | Open Source | Open source software. Limited commercial support for maintenance and patching. |
| CoolKey | Linux, *nix versions vary | Open Source | |
| CACKey | Linux, *nix versions vary | US Government Source | Available from Forge.mil |
| Commercial options | Varies | Yes | Review support for your usage needs such as email signing, encryption, network authentication, VPNs, and website authentication |
You may need to consider network authentication, Virtual Private Network (VPN), email signing, email encryption, document signing, document encryption and website authentication when choosing one or more middleware options for yourself or your users. In most cases, you can choose a middleware option that works for the most common uses for your purposes or mix and match based on operating systems and devices.
Middleware Definitions
Middleware as a general computer term can encompass any software that provides integration points for an application. In the standards for PIV credentials, the term PIV middleware is used. A common question is “What is the difference between PIV middleware and general smart card middleware?” To simplify, we’ll define the two terms as we use them for PIV credentials in these guides:
PIV Middleware:
Client side software which implements the full set of application programming interfaces and card functions as specified in NIST Special Publication 800-73-4 and has been certified as compliant with the NIST Special Publication 800-85A series testing procedures. The PIV compliant middleware implements all lifecycle functions, including a user’s ability to perform PIN resets, activation, and renewals. The PIV compliant middleware may also implement common usage functions to support authentication, digital signatures, encryption, and integrations with multiple operating system cryptographic libraries.
General Smart Card Middleware:
Client side software which implements common functions for an operating system and cryptographic libraries to interface with PIV credentials or other smart cards for usage. The general smart card middleware may implement functions to support authentication, digital signatures, encryption, and integrations with multiple operating system cryptographic libraries.
For common PIV credential usage scenarios, we outline the general smart card middleware available as open or government source or included in operating systems for use scenarios. Commercial options for PIV middleware are available and the list of NIST-certified PIV middleware can be viewed here on the NIST website.
PIV Credential Certificate Types
Viewing the certificate information on your PIV credential may be interesting if you are a general user. You must understand certificate information as a program manager or engineer developing applications and designing solutions for using PIV credentials.
Within the U.S. federal government, the certificate and PIV credential information is governed by standards, policies, and implementation-specific choices (options) across all agency credential providers.
Typically, there are four certificates and four key pairs on a PIV credential. However, one pair (i.e., one certificate and one key pair) is ALWAYS on every PIV credential and three pairs (i.e., three certificates and three key pairs) are SOMETIMES on a PIV credential. You can review the PIV Overview to view the four pairs and purposes.
The table below outlines the general information for the PIV credential certificates, certificate extensions, and design considerations.
6 Years
PIV credentials and certificates have changed over time due to updates in standards. Since users may have credentials for up to 6 years and there are both optional and mandatory elements, the information presented is what is valid for ALL PIV credentials and certificates currently in use. (Although credentials are valid for 6 years, the certificates contained on a credential are valid for only 3 years, with the exception of the content signer.)
| Certificate | Required | Key Usage | Extended Key Usage | Subject Alternative Name | Design Considerations |
|---|---|---|---|---|---|
| PIV Authentication | Always | Digital Signature | Client Authentication | otherName = FASC-N; uniformResourceIdentifier = UUID; Principal Name = prefix@suffix |
Principal Name values are not required by policy to be present in all Subject Alternative Name extensions. The Card UUID may also commonly be referred to as the Global Unique Identifier (GUID). |
| Card Authentication | Always | Digital Signature | id-PIV-cardAuth | Name = FASC-N; uniformResourceIdentifier = UUID |
Card Authentication must be included in new and replacement PIV credentials issued after August 2014; it is not expected that all PIV credentials will have Card Authentication certificates until September 2019. The Card UUID may also commonly be referred to as the GUID. |
| Digital Signature | Sometimes | Digital Signature, Non-Repudiation | Specific EKUs are required for certificates issued after June 2019 | rfc822name = email address | Email address is not required by policy. Email address may be multivalued attributes and include email aliases. |
| Encryption | Sometimes | Key Encipherment | Specific EKUs are required for certificates issued after June 2019 | rfc822name = email address | Email address is not required by policy. Encryption certificates that represent available, retired encryption key pairs may exist, depending on the PIV issuer. |
| PIV Content Signer | Always | Digital Signature | id-PIV-content-signing | N/A | The PIV content signer ensures the integrity of the digital information stored on the card. Physical Access Control Systems (PACS) are the primary relying party for these certificates. This certificate is unavailable in most logical trust stores, but users can leverage the Card Conformance Tool (CCT if they would like to extract and view the PIV content signing certificate. |
How to View PIV Credential Certificates
You can use these simple methods to view, export, and understand the information stored on a PIV credential.
Keys are safe!
Don’t worry; the public certificates are public. The private keys are always stored safely on your PIV credential and can never be exported.
View Your PIV Credential Certificates
Almost all of the methods for using your PIV credential for networks, applications, digital signatures, and encryption involve the certificates and key pairs stored on your PIV credential. There are also scenarios where additional information (such as biometrics) is also accessed and used.
To view your certificate information:
- Insert your PIV credential into your card reader.
- Choose an option from the table below and follow the steps.
| Operating System | Module | Steps |
|---|---|---|
| Microsoft | Internet Explorer | Open Internet Explorer Browser > Tools Wheel or (Alt+X) > Internet Options > Content Tab > Certificates Button > Personal Tab |
| Microsoft | Microsoft Management Console (MMC) and Certificate Snap-in | Open Microsoft Management Console > File > Add/Remove Snap-In > Certificates Snap-in > Add > My user account > Finish > Expand Certificates - Current User > Personal > Certificates |
| Any | Chrome Browser | Open Chrome Browser > Settings > Show Advanced Settings > Manage Certificates (Manage HTTPS/SSL Certificates and Settings) > Personal tab |
| Any | Firefox Browser | Open Firefox Browser > Settings wheel > Privacy & Security > Security > Certificates > View Certificates button > Certificates Manager > Your Certificates Tab |
| macOS X | Keychain | Open Applications > Utilities > Keychain Access > Select Login > Categories > My Certificates |
View
You may see many certificates. To open and view the certificate details, double-click on any certificate.
Export
Look for an Export button and save the file as DER or PEM-encoded, with a file extension of cer (.cer).
Additional useful information:
- All key pairs for users are 2048-bit (RSA) keys.
- All certificates issued and certified as PIV are SHA-256 signed.
- If you are working with Common Access Cards, you may still encounter SHA-1-signed certificates and might not see a Card Authentication certificate.
- There has been testing in some infrastructures to migrate to Elliptic Curve Cryptography (ECC), but there are no ECC certificates for users in production as of the date of this guide.
- There has been testing in some infrastructures to migrate to 3072-bit (RSA) certificates, but there are no 3072-bit certificates for users in production as of the date of this guide.
In-depth details on the certificate profiles are contained in the current and historical Federal Public Key Infrastructure (FPKI) policy documents. The most recent policy and certificate profile documents may be found on IDManagement.gov’s FPKI Policy and Compliance Audit page.
PIV Unique Identifiers
In applications including network domains, you will associate the PIV credential with your accounts. This process is not unique to PIV credentials and usage; it is a general concept that occurs in many applications, including your personal email accounts, your bank accounts, or your favorite social media app.
Associating a credential with an account is called account linking.
Identifiers are the values in credentials that are used for account linking. We focus on the PIV Authentication certificate and identifiers in this section to help you understand the options and design and implement solutions for using PIV to authenticate to networks and applications. For more information on account linking, see Account Linking .
The table below outlines identifiers available in the PIV Authentication certificate and design considerations for implementations.
| Identifiers | Considerations |
|---|---|
| Subject | Unique for every person within the same agency; value does not change when a user receives a new, replaced, or updated PIV credential within the same agency. |
| Issuer and Subject | Unique for every person; value does not change when a user receives a new, replaced, or updated PIV credential within the same agency. |
| Issuer and Serial Number | Unique for every person and certificate; value changes when a user receives a new, replaced, or updated PIV credential. |
| Subject Key Identifier | Unique for every person and certificate; value changes when a user receives a new, replaced, or updated PIV credential. |
| SHA-1 Hash of Public Key | Value changes when a user receives a new, replaced, or updated PIV credential; commonly referred to as the thumbprint of the certificate. |
| Federal Agency Smart Card Number (FASC-N) | It is not recommended to use the FASC-N as an identifier; unique for every credential only within the U.S. federal Executive Branch agencies; no uniqueness for PIV credentials issued by Legislative or Judicial Branch agencies, state, local, tribal, territories, partners, or any credentials certified as PIV-Interoperable or PIV-I; value changes when a user receives a new, replaced, or updated PIV credential; legacy definition and usage supported building access control systems as outlined in Technical Implementation Guidance: Smart Card Enabled Physical Access Control Systems) (PDF, 2005). |
| Card Universal Unique Identifier (UUID) | Unique for every person and credential; value changes when a user receives a new, replaced, or updated PIV credential; Card UUID value is only required to be present for new or replacement PIV credentials issued after August 2014; may also commonly be referred to as the Global Unique Identifier (GUID). |
| User Principal Name in Subject Alternate Name | Not required to be included in all PIV Authentication certificates; not recommended for use as an identifier to achieve full interoperability for networks or applications; commonly used for enterprise smart card logon / network authentication in legacy implementations. |
For all items referencing an agency in the table, you should consider the reference as the small organizational unit. For example, a user who switches between one component in a large agency to another component may receive a new Subject Name when the user requires a replacement PIV credential.
Organization Specific Identifiers
Multiple departments and agencies leverage a persistent, internal unique identifier. For example, the Department of Defense uses a unique 10-digit identifier called the Electronic Data Interchange Personal Identifier or EDIPI. The Department of Homeland Security and the Department of Health and Human Services leverage a similar persistent lifetime identifier for their identities. Note that these identifiers are unique within the systems that generate them. There is a risk of collision when leveraging these identifiers in external systems.


